This method is a more troublesome method , But it doesn't need the cooperation of browser , Suitable for reptiles and the like .
And another kind. , Use webdriver Of , It is simpler to use than this , It can be used for daily check-in 、 Punch in and so on , Use python + Relevant browsers webdriver Drive the browser to operate .
This development is in Windos and Linux Both are successful , The operating environment is :
Linux:python 3.7.2
Windows:python 3.7.1
Be careful , stay Linux Next make install When , Be sure to install it in advance ssl、zlib etc. , The former makes python Support https, The latter ensures smooth installation . Don't forget gcc Also install in advance .
Possible solutions to the above two problems :
yum install openssl-devel
yum install zlib*
This simulation website :https://www.bbaaz.com
Its login interface website is :https://www.bbaaz.com/member.php?mod=logging&action=login
First use the browser to open , enter one user name 、 password , then F12 open Dev Tools, choice Network tab , Pay attention to check Preserve log, Otherwise, the possible situation is , You click login , because package Too many reasons , Or jump to a new page , The key package has been discarded .
Find the key package , Here's the picture , You can see a lot of information .
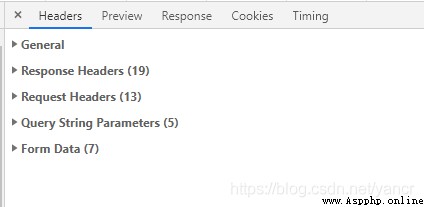
from package You can get :
Request URL: https://www.bbaaz.com/member.php?mod=logging&action=login&loginsubmit=yes&loginhash=Lm0Hi&inajax=1
Set-Cookie:xxxxx
Form Data
formhash: xxxxx
referer: https://www.bbaaz.com/
loginfield: username
username: xxxxx
password: xxxxx
questionid: 0
answer:
Observe carefully , What was found , First ,Request URL With a loginhash, Again Form Data With formhash, These should prevent illegal login , So where did these data come from ? Logged off , Reopen the login interface , Analysis login interface , You can know this information , Are hidden information of the original login interface .
So our idea is , First , Open the login interface , Get two from the login interface Hash value , Open another one to store Cookie Of Request, Login to URL Send the form , Record the returned Cookie, When you open another page , You can go through Cookie Visit .
import urllib.request
import http.cookiejar
form = {'formhash': '',
'referer': 'https://www.bbaaz.com/',
'loginfield': 'username',
'username': 'xxxxx',
'password': 'xxxxx',
'questionid': '0',
'answer': ''}
headers = {'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3562.0 Safari/537.36'}
loginURL = "https://www.bbaaz.com/member.php?mod=logging&action=login"
query = "&loginsubmit=yes&frommessage&loginhash=xxx&inajax=1"
""" Why did you use the belt directly at the beginning Cookie Of opener Well , After testing , When opening the login interface , The server will send... To the client 3 individual Cookie, these Cookie It also has the function of verification , If you don't bring , When logging in , The server will return , Contains illegal characters , Unable to login """
cookie = http.cookiejar.CookieJar()
opener = urllib.request.build_opener(urllib.request.HTTPCookieProcessor(cookie))
req = urllib.request.Request(loginURL, headers = headers)
resp = opener.open(req)
s = resp.read().decode('utf-8')
# Get the login interface Hash value
s = s.split('<form method=\"post\"', 1)[1].split('name=\"formhash\" value=\"', 1)
suffix = s[0].split("loginform_", 1)[1].split("\"", 1)[0]
formhash = s[1].split("\" />", 1)[0]
query = query.replace('xxx', suffix)
form['formhash'] = formhash
post_form = urllib.parse.urlencode(form).encode('UTF-8')
req = urllib.request.Request(loginURL + query, headers = headers, data = post_form)
opener.open(req)
# The web page you want to visit
req = urllib.request.Request(form['referer'], headers = headers)
resp = opener.open(req)
s = resp.read().decode('UTF-8')
After testing , Using this method , Successfully simulated Login .
https://blog.csdn.net/yancr/article/details/88762380