Recently, I received a network security book presented by the electronic industry press 《python Black hat 》, There are a total of 24 An experiment , Today, I will repeat the 22 An experiment ( wmi Process monitoring ), My test environment is windows10 virtual machine (64 position )+conda development environment +python3.7. This experiment can monitor windows Processes running in the system , It is helpful to collect the startup information of each process , It is convenient to analyze the quality of the process ~
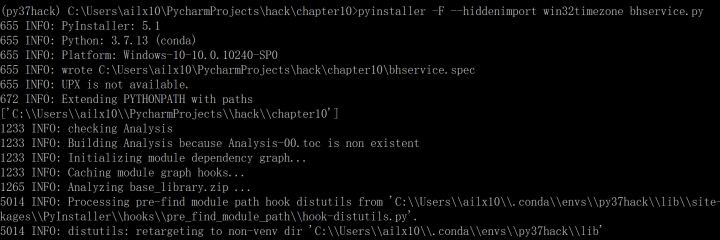
1、 stay py37hack Environment , take python Script compiled into exe Executable program
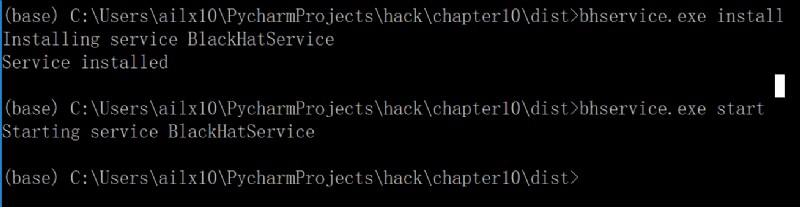
2、 Get into dist Install and run in the directory bhservice service
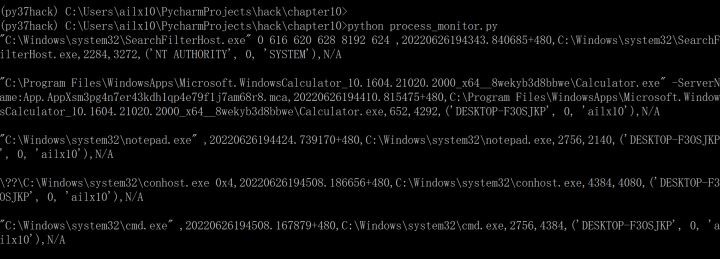
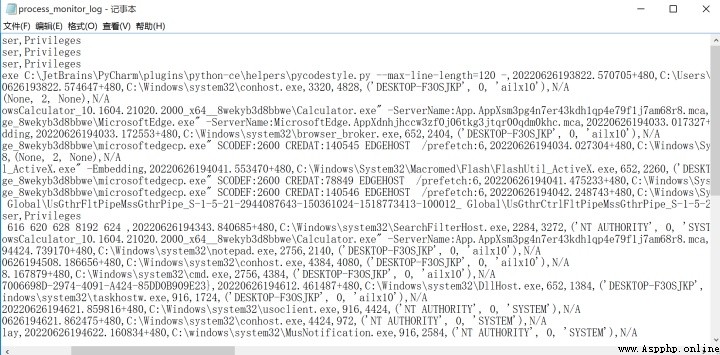
3、 above 2 Steps can be ignored , Start using... Here WMI Monitor progress , function monitor Script , You can monitor all the processes that run later , Here I tested calc Calculator 、notepad Notepad 、cmd Command line , All successful , Here you can see that the user name of the computer is recorded 、 process PID、 There is also information such as the file location of the process , very nice ~
4、 Have a coffee , wait a while , Open... In the directory where the script is located txt file , Check what the computer did secretly , There are many records here ~
Reference code :
# -*- coding: utf-8 -*-
# @Time : 2022/6/26 7:10 PM
# @Author : ailx10
# @File : process_monitor.py
import os
import sys
import win32api
import win32con
import win32security
import wmi
def log_to_file(message):
with open("process_monitor_log.csv","a") as fd:
fd.write(f"{message}\r\n")
def monitor():
head = "CommandLine,Time,Executable,Parent,PID,PID,User,Privileges"
log_to_file(head)
c = wmi.WMI()
process_watcher = c.Win32_Process.watch_for("creation")
while True:
try:
new_process = process_watcher()
cmdline = new_process.CommandLine
create_date = new_process.CreationDate
executable = new_process.ExecutablePath
parent_pid = new_process.ParentProcessId
pid = new_process.ProcessId
proc_owner = new_process.GetOwner()
privileges = "N/A"
process_log_message = (f"{cmdline},{create_date},{executable},{parent_pid},{pid},{proc_owner},{privileges}")
print(process_log_message)
print()
log_to_file(process_log_message)
except Exception:
pass
if __name__ == "__main__":
monitor()