Recently, I received a network security book presented by the electronic industry press 《python Black hat 》, There are a total of 24 An experiment , Today, I will repeat the 11 An experiment ( Face recognition ), My test environment is mbp The computer +conda development environment . This experiment is followed by the restoration of the previous traffic picture , The traffic image restoration can be connected to the man in the middle attack , In this way, you can sniff what the target is browsing , For example, pornographic websites , So as to create a breakthrough for social engineering fraud and extortion ~
1、 First, go to the Internet and randomly search for several face pictures , I was going to put all the pictures of beautiful women , Here is a tribute to the industry leaders @ Subtly malicious 、@kn1f3

2、 Download prerequisite xml The configuration file
wget https://eclecti.cc/files/2008/03/haarcascade_frontalface_alt.xml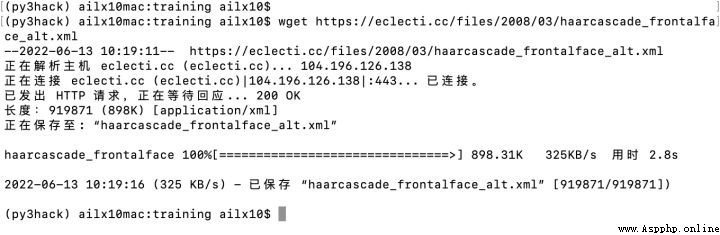
3、 stay mbp Run the script on
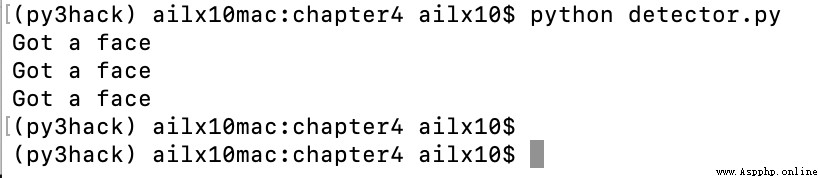
4、 stay faces View face results in folder

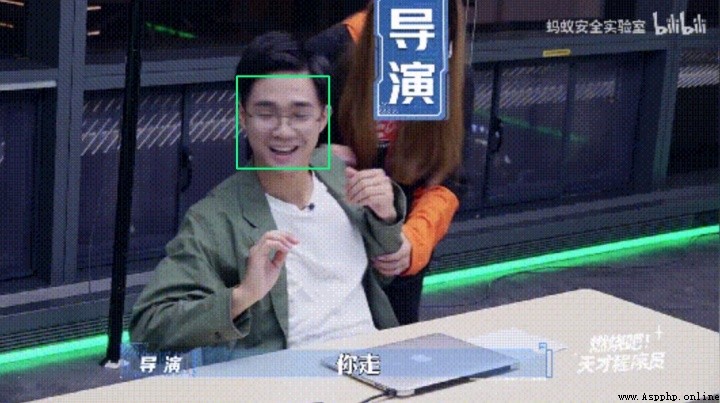

Reference code :
# -*- coding: utf-8 -*-
# @Time : 2022/6/13 7:36 PM
# @Author : ailx10
# @File : detector.py
import cv2
import os
ROOT = "/Users/ailx10/py3hack/chapter4/picture"
FACES = "/Users/ailx10/py3hack/chapter4/faces"
TRAIN = "/Users/ailx10/py3hack/chapter4/training"
def detect(srcdir=ROOT,tgtdir=FACES,train_dir=TRAIN):
for fname in os.listdir(srcdir):
if not fname.upper().endswith(".JPG"):
continue
fullname = os.path.join(srcdir,fname)
newname = os.path.join(tgtdir,fname)
img = cv2.imread(fullname)
if img is None:
continue
gray = cv2.cvtColor(img,cv2.COLOR_BGR2GRAY)
training = os.path.join(train_dir,"haarcascade_frontalface_alt.xml")
cascade = cv2.CascadeClassifier(training)
rects = cascade.detectMultiScale(gray,1.3,5)
try:
if rects.any():
print("Got a face")
rects[:,2:] += rects[:,:2]
except AttributeError:
print(f"No face found in {fname}")
continue
for x1,y1,x2,y2 in rects:
cv2.rectangle(img,(x1,y1),(x2,y2),(127,255,0),2)
cv2.imwrite(newname,img)
if __name__ == "__main__":
detect()