after 10 About Python Font anti crawl series , We have entered a new theme , Common confusion encryption principle and practice .
This blog is from eval Confusion starts , Disassemble for everyone layer by layer JS Confusing related knowledge in reverse .
eval The function can change JS The string is parsed into the source code for execution
Random selection in the search engine can be encrypted JS Code page , Then encrypt the following .
Before encryption
var name = " Eraser ";
After encryption
eval(
(function (p, a, c, k, e, d) {
e = function (c) {
return (
(c < a ? "" : e(parseInt(c / a))) +
((c = c % a) > 35 ? String.fromCharCode(c + 29) : c.toString(36))
);
};
if (!"".replace(/^/, String)) {
while (c--) d[e(c)] = k[c] || e(c);
k = [
function (e) {
return d[e];
},
];
e = function () {
return "\\w+";
};
c = 1;
}
while (c--)
if (k[c]) p = p.replace(new RegExp("\\b" + e(c) + "\\b", "g"), k[c]);
return p;
})('1 0 = " Eraser "', 62, 2, "name|var".split("|"), 0, {
})
);
You can see that the encrypted code becomes more complex , And the readability becomes weak .
stay JS in ,eval The function itself is a JS Code executor , It can convert the incoming string into JS Syntax is parsed and executed .
Decrypt eval The method of function is relatively simple , Find the tools directly .
The most common scenario for this form of code is Baidu's statistical code , You can look for specific cases .
The site we want to collect this time is TV cat , The target address is :https://www.tvmao.com/program/BTV1.
After clicking more on this page , Program list data will be loaded , The interface and parameters obtained are as follows .
By viewing more , We can grab the data request location .
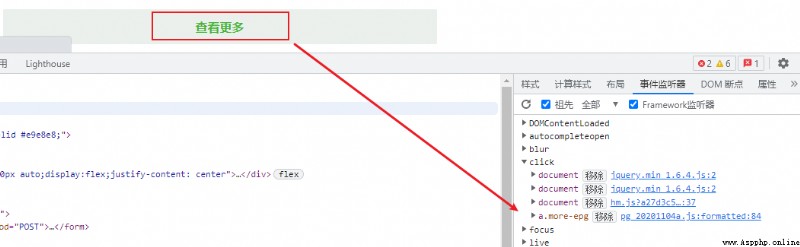
Accompanying breakpoints , We enter JS Reverse link , The first code obtained is as follows .
$(".more-epg").click(function () {
var b = "src";
var a = A.d("a", b);
ajaxVerify(
"/api/pg",
"GET",
{
p: a,
},
function (c, d) {
$("#noon").after(d[1]);
$(".more-epg").remove();
}
);
});
The core of the code is A.d("a", b) , The function d() It may be an encryption link .
Next is the main content , We did not find the location of the encryption function JS file , The JS Code snippets are temporary , Or anonymous .
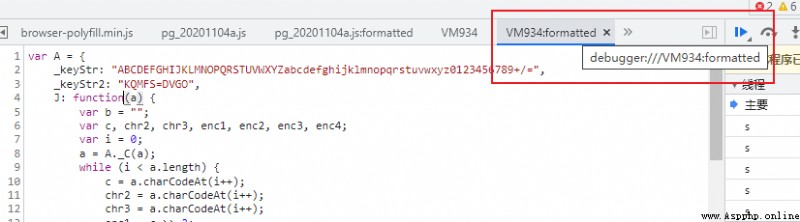
But the keyword _keyStr Can be directly retrieved , Search the whole picture , Get the following .
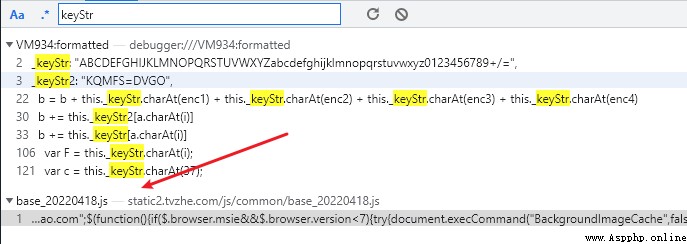
Along base.js Climb over , Find the following , Find out eval function , The point of confusion appears .
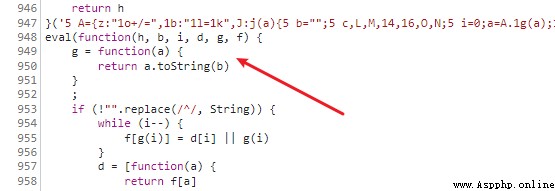
be-all eval Function wrapped code , You can use console.log Print .
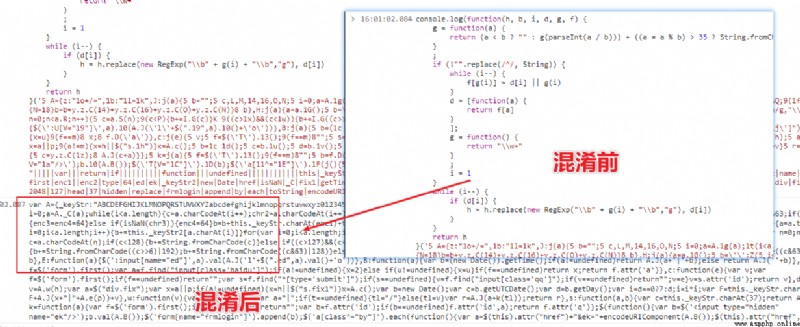
You can see the code differences before and after the confusion , After parsing, it happens to be our objective function .
You can also search for anti aliasing tools , Direct inquiry is enough , Anti confusion , Pay attention to carrying eval() function , The content can be tested many times by yourself .
When we get the original function , The basic representation encryption logic has been solved .
Finally, I'd like to add
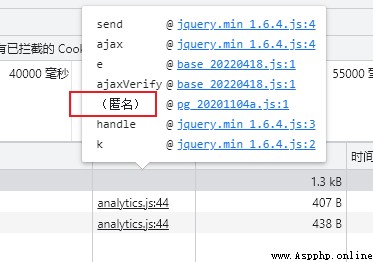
When you find out 【 anonymous 】 Function time , Probably this paragraph JS Is an encrypted string .
You are reading 【 Dream eraser 】 The blog of
Finished reading , You can praise it with a little hand
Find the error , Correct it in the direct comment area
The second part of the eraser 683 Original blog