本博客地址:https://blog.csdn.net/wutianxu123/article/details/125397313
當可以遠程訪問內網中的某台SSH服務器時,如果此時的目的是內網中一台web服務器,當無法訪問那台web服務器,而這台可以訪問的SSH服務器又沒有安裝一些工具,我們就可以配置一條反向SSH隧道連接(如果沒有SSH服務的話)。
要搭建這種隧道,必須先像往常一樣,從內網的Windows客戶端連到外網的SSH服務器上。通過這條SSH連接,我們可以在服務器上的某個遠程端口和本地端口之間建立一條隧道。通過這個本地端口,我們可以暴露某個內部系統的3389端口並通過遠程桌面協議訪問,或者訪問這台Windows設備能訪問的任何系統。
Paramiko的官方示例中有個rforward.py程序,位置在:paramiko-main\demos\rforward.py,可以直接使用。
已經對核心部分做了中文注釋。代碼如下:
#!/usr/bin/python
#-*- coding:utf8 -*-
import getpass
import os
import socket
import select
import sys
import threading
from optparse import OptionParser
import paramiko
SSH_PORT = 22
DEFAULT_PORT = 4000
g_verbose = True
# 管理每個線程的通信
def handler(chan, host, port):
sock = socket.socket()
try:
sock.connect((host, port))
except Exception as e:
verbose("Forwarding request to %s:%d failed: %r" % (host, port, e))
return
verbose(
"Connected! Tunnel open %r -> %r -> %r"
% (chan.origin_addr, chan.getpeername(), (host, port))
)
# 完成數據的收發
while True:
r, w, x = select.select([sock, chan], [], [])
if sock in r:
data = sock.recv(1024)
if len(data) == 0:
break
chan.send(data)
if chan in r:
data = chan.recv(1024)
if len(data) == 0:
break
sock.send(data)
chan.close()
sock.close()
verbose("Tunnel closed from %r" % (chan.origin_addr,))
def reverse_forward_tunnel(server_port, remote_host, remote_port, transport):
# transport負責建立和維持加密通信
# request_port_forward將服務器上某個端口的TCP連接全部轉發過來
transport.request_port_forward("", server_port)
while True:
# channel加密transport會話中收發的數據
# 建立一個新的channel
chan = transport.accept(1000)
if chan is None:
continue
# 調用handler函數處理這個channel
thr = threading.Thread(
target=handler, args=(chan, remote_host, remote_port)
)
thr.setDaemon(True)
thr.start()
def verbose(s):
if g_verbose:
print(s)
HELP = """\ Set up a reverse forwarding tunnel across an SSH server, using paramiko. A port on the SSH server (given with -p) is forwarded across an SSH session back to the local machine, and out to a remote site reachable from this network. This is similar to the openssh -R option. """
def get_host_port(spec, default_port):
"parse 'hostname:22' into a host and port, with the port optional"
args = (spec.split(":", 1) + [default_port])[:2]
args[1] = int(args[1])
return args[0], args[1]
# 參數聲明
def parse_options():
global g_verbose
parser = OptionParser(
usage="usage: %prog [options] <ssh-server>[:<server-port>]",
version="%prog 1.0",
description=HELP,
)
parser.add_option(
"-q",
"--quiet",
action="store_false",
dest="verbose",
default=True,
help="squelch all informational output",
)
parser.add_option(
"-p",
"--remote-port",
action="store",
type="int",
dest="port",
default=DEFAULT_PORT,
help="port on server to forward (default: %d)" % DEFAULT_PORT,
)
parser.add_option(
"-u",
"--user",
action="store",
type="string",
dest="user",
default=getpass.getuser(),
help="username for SSH authentication (default: %s)"
% getpass.getuser(),
)
parser.add_option(
"-K",
"--key",
action="store",
type="string",
dest="keyfile",
default=None,
help="private key file to use for SSH authentication",
)
parser.add_option(
"",
"--no-key",
action="store_false",
dest="look_for_keys",
default=True,
help="don't look for or use a private key file",
)
parser.add_option(
"-P",
"--password",
action="store_true",
dest="readpass",
default=False,
help="read password (for key or password auth) from stdin",
)
parser.add_option(
"-r",
"--remote",
action="store",
type="string",
dest="remote",
default=None,
metavar="host:port",
help="remote host and port to forward to",
)
options, args = parser.parse_args()
if len(args) != 1:
parser.error("Incorrect number of arguments.")
if options.remote is None:
parser.error("Remote address required (-r).")
g_verbose = options.verbose
server_host, server_port = get_host_port(args[0], SSH_PORT)
remote_host, remote_port = get_host_port(options.remote, SSH_PORT)
return options, (server_host, server_port), (remote_host, remote_port)
def main():
# 會檢查必需的幾個參數是否都傳進來了
options, server, remote = parse_options()
password = None
if options.readpass:
password = getpass.getpass("Enter SSH password: ")
# 創建一個Paramiko的SSH客戶端連接
client = paramiko.SSHClient()
client.load_system_host_keys()
client.set_missing_host_key_policy(paramiko.WarningPolicy())
verbose("Connecting to ssh host %s:%d ..." % (server[0], server[1]))
try:
client.connect(
server[0],
server[1],
username=options.user,
key_filename=options.keyfile,
look_for_keys=options.look_for_keys,
password=password,
)
except Exception as e:
print("*** Failed to connect to %s:%d: %r" % (server[0], server[1], e))
sys.exit(1)
verbose(
"Now forwarding remote port %d to %s:%d ..."
% (options.port, remote[0], remote[1])
)
try:
reverse_forward_tunnel(
options.port, remote[0], remote[1], client.get_transport()
)
except KeyboardInterrupt:
print("C-c: Port forwarding stopped.")
sys.exit(0)
if __name__ == "__main__":
main()
命令:
python rforward.py 192.168.153.141 -p 8081 -r 192.168.153.140:3000 --user=kali --password
備注:
192.168.153.141,是SSH服務器的IP
192.168.153.140,是web服務器的IP
--user,是SSH服務器的用戶名
--password,是SSH服務器的密碼
運行效果:
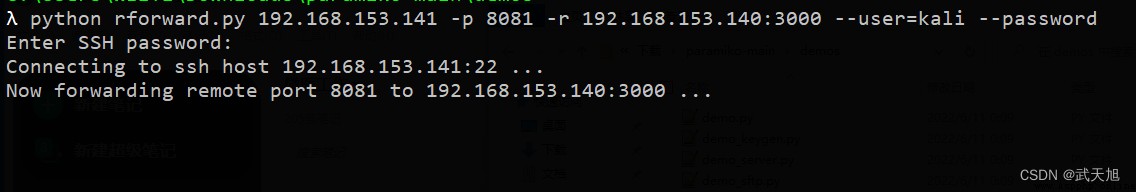
我們連接了SSH服務器,並在上面打開了8081端口,這個端口會將流量都轉發到web服務器的3000端口上,現在在SSH服務器上訪問http://127.0.0.1:8081,會通過SSH隧道連接到位於web服務器上的3000端口上的web服務。