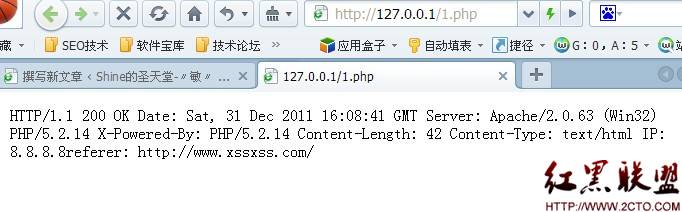
效果如圖
偽造的文件:1.php
<?php
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, "http://localhost/2.php");
curl_setopt($ch, CURLOPT_HTTPHEADER, array('X-FORWARDED-FOR:8.8.8.8', 'CLIENT-IP:8.8.8.8')); //構造IP
curl_setopt($ch, CURLOPT_REFERER, "http://www.xssxss.com/ "); //構造來路
curl_setopt($ch, CURLOPT_HEADER, 1);
$out = curl_exec($ch);
curl_close($ch);
?>
查看效果的腳本2.php
<?php
function getClientIp() {
if (!empty($_SERVER["HTTP_CLIENT_IP"]))
$ip = $_SERVER["HTTP_CLIENT_IP"];
else if (!empty($_SERVER["HTTP_X_FORWARDED_FOR"]))
$ip = $_SERVER["HTTP_X_FORWARDED_FOR"];
else if (!empty($_SERVER["REMOTE_ADDR"]))
$ip = $_SERVER["REMOTE_ADDR"];
else
$ip = "err";
return $ip;
}
echo "IP: " . getClientIp() . "";
echo "referer: " . $_SERVER["HTTP_REFERER"];
摘自 www.xssxss.com/fuck/519.xss